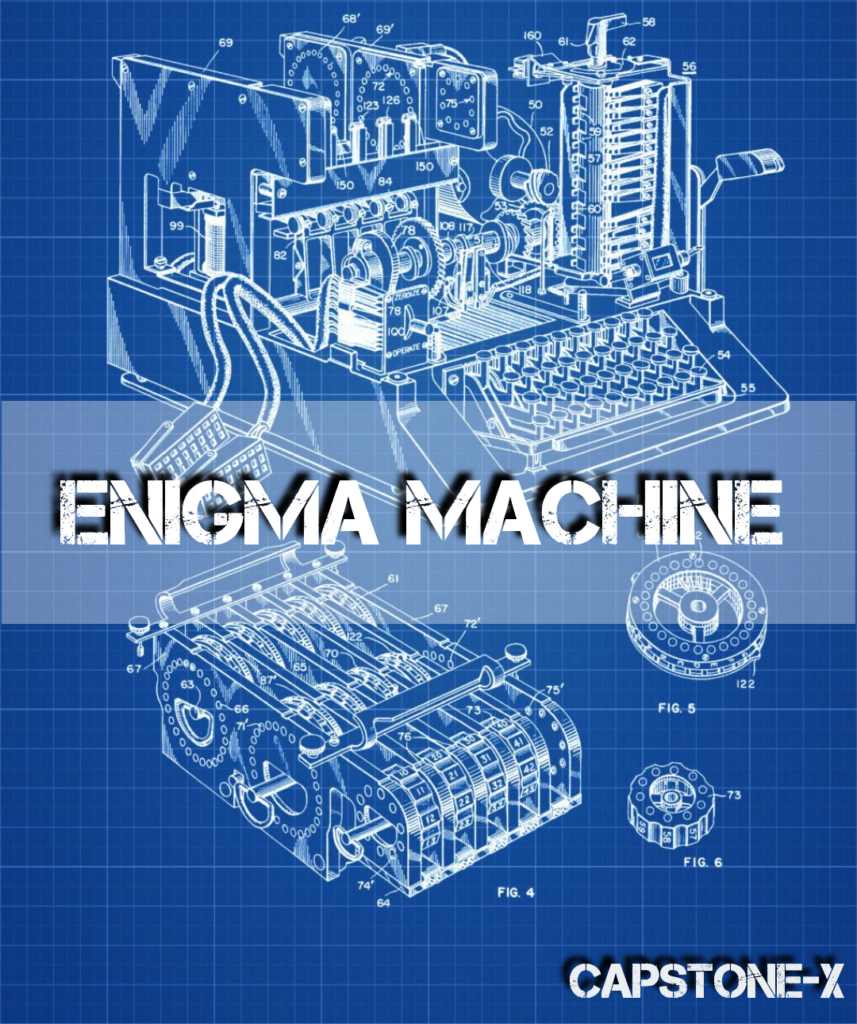
An Enigma machine is a famous encryption machine used by the Germans to transmit coded messages during WWII. An Enigma machine can encrypt a message in billions of different ways, making it extremely difficult for other nations to decipher German codes during the war — for a while, the code appeared unbreakable. But Alan Turing and other researchers exploited a few flaws in the Enigma code implementation and gained access to German codebooks, allowing them to construct the Bombe machine, which assisted in cracking the most difficult versions of Enigma.

It used a sequence of rotors to allow the operator to encrypt or decrypt a message using electricity, a light bulb, and a reflector. The original position of the rotors, which was set with each encryption and was based on a preset sequence that was dependent on the calendar, allowed the machine to be utilized even if it was compromised.

When the Enigma was in use, with each consecutive key press, the rotors would shift out of alignment from their predetermined places, producing a different letter each time. The operator would enter each character into the machine by pressing a typewriter-like key while holding a message in his hand. The rotors would align, and a letter would illuminate, informing the operator of what the letter was. Similarly, during enciphering, the operator presses the key, and the lit letter is the cipher text. The constantly changing internal flow of electricity that caused the rotors to alter was not random, but it did create a polyalphabetic cipher that was unique each time it was employed.
Enigma Encryption
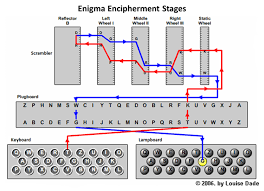
Enigma employs a type of substitution cipher. When the rotors turn, a new set of three numbers/letters appears. A message recipient can decode the message using the initial set of three numbers/letters (meaning the numbers/letters on the sender’s machine when they began typing the message) by setting their (identical) Enigma machine to the initial settings of the sender’s Enigma machine. Each rotor contains 2626 numbers/letters. The Germans were able to switch rotors, selecting from a set of five, resulting in thousands of different combinations for an Enigma system.
Substitution encryption is a simple method of encoding communications, although these codes are quite easy to crack. A Caesar cipher is a simple example of a substitution encryption technique. A Caesar cipher changes each letter of the alphabet by a certain number of positions. With a shift of 11, a Caesar cipher would encode an A as a B, a M as an N, and a Z as an A, and so on.
For Example: using the simple substitution method “Capstonex” with a shift of 5 can be encrypted with this scheme as : “hfuxytsjc”
For the real Enigma “Capstone-X” is written as “WRFO UADZ Y”.
Use this converter to encrpt to Enigma: https://v2.cryptii.com/text/enigma
Share with us your encrypted name in the comments.

However, Enigma devices are far more powerful than simple Caesar ciphers. Consider how the entire encoding scheme would change each time a letter was mapped to another. The rotors move after each button push, and pressing the same button again conducts current along a new path to a different revealed letter.
Mechanism of Enigma:
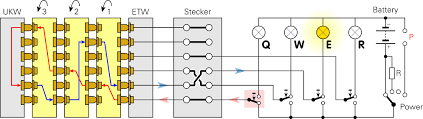
Encoded messages would be a certain scramble of letters on a specific day that would convert to an understandable sentence when unscrambled. When a key is pressed on the keyboard, one or more rotors move to establish a new rotor configuration that encodes one letter as another. Current runs through the machine, lighting up one of the lamp board’s display lamps, which displays the output letter. So, if the “K” key is hit and the Enigma machine encodes that letter as a “P,” the “P” on the lamp board will light up. Enigma operators got codebooks every month that stated which settings the machine would use each day. The coding would vary every morning.
There are three main parameters or configurations to set:
– Plugboard settings: A/L-P/R-T/D-B/W-K/F-O/Y
– Rotor (or scrambler) arrangement: 2-3-1
– Rotor orientation: D-K-P
To know more details visit this website: https://brilliant.org/wiki/enigma-machine/
How Enigma was Cracked?

The Enigma code had a severe weakness in that a letter could never be encoded as itself. In other words, a “M” would never be encoded as a “M,” which was a major problem in the Enigma code because it provided codebreakers with information that might be used to decrypt messages. If the codebreakers could guess a word or phrase that would most likely appear in the message, they may begin breaking the code. Because the Germans routinely delivered a weather report at the start of the letter and usually included the phrase “Heil Hitler” at the end, decrypters understood what to look for.
Decoders could compare a given phrase to the letters in the code, and if a letter in the phrase matched one in the code, they knew that part of the code did not include the phrase. The decoders might then start cracking the code through a process of elimination.

Alan Turing and Gordon Welchman created the Bombe machine, which employed electric circuits to decipher an Enigma encoded message in less than 20 minutes. The Bombe machine would attempt to determine the settings of the Enigma machine’s rotors and plugboard used to convey a specific coded message.
The conventional British Bombe machine was simply 36 Enigma devices connected together to simulate numerous Enigma machines at the same time. The majority of Enigma machines had three rotors, and to mimic this in the Bombe, each Enigma simulator had three drums, one for each rotor.
Types of Enigma Machine:

A selection of seven Enigma machines and paraphernalia exhibited at the USA’s National Cryptologic Museum. From left to right, the models are: 1) Commercial Enigma; 2) Enigma T; 3) Enigma G; 4) Unidentified; 5) Luftwaffe (Air Force) Enigma; 6) Heer (Army) Enigma; 7) Kriegsmarine (Naval) Enigma — M4.
Enigma Blurprints:

Check the links below to view the blueprints:
– Blueprint of Rack: http://enigma.hs-weingarten.de/downloads/rack_10.pdf
– Blueprint of Reflector: http://enigma.hs-weingarten.de/downloads/reverse_roll_300.pdf
– Blueprint of Rotor: http://enigma.hs-weingarten.de/downloads/roll_400.pdf
Data Security Nowadays:

Today, mathematics is at the heart of keeping all of our electronic data secure and preventing hacking efforts. As hackers methods for discovering information become more complex and the systems they use to attack information become faster, cyber security is a never-ending race to develop new and better ways to protect information.
Written by Hassan Nasser
5 September 2022
Refrences:
– Enigma machine. Brilliant Math & Science Wiki. (n.d.). Retrieved September 5, 2022, from https://brilliant.org/wiki/enigma-machine/
– Enigma machine. Enigma Machine – an overview | ScienceDirect Topics. (n.d.). Retrieved September 5, 2022, from https://www.sciencedirect.com/topics/computer-science/enigma-machine
– Enigma cipher machine. Learning. (2020, October 2). Retrieved September 5, 2022, from https://learning.sciencemuseumgroup.org.uk/resources/enigma-cipher-machine-3d-object/